How (and Why) to Obfuscate Source Code and What is New You Can Accomplish in 2025
Table of Contents
Protect your business today!
Get a QuoteProtect your business today!
Get a QuoteThe deliberate action to obfuscate source code refers to the intentional transformation of programmatic logic into a form that is exceedingly difficult for humans to interpret, while remaining functionally identical from the standpoint of machine execution. This technique, while deceptively simple in conceptual premise, occupies a crucial position at the intersection of cybersecurity, intellectual property protection, and strategic business operations in the digital age.
Obfuscation is not encryption, though the two are often conflated. Whereas encryption renders data entirely unreadable until decrypted—thereby necessitating additional runtime processes to restore operability—obfuscation preserves the code’s machine operability while simultaneously degrading its legibility to human observers. It is, in essence, a form of asymmetric information architecture: intelligible to the machine, opaque to the adversary.
Developers and technology firms employ code obfuscation for a variety of interrelated purposes. Primarily, it serves to safeguard proprietary logic from reverse engineering, thereby impeding intellectual property theft. It also introduces substantial barriers to tampering and unauthorized modification—particularly important in contexts where software is deployed in hostile or semi-trusted environments. Furthermore, obfuscation can obscure business-critical algorithms, data flows, or security mechanisms, thus raising the cost of cyber intrusion for would-be attackers.
In the competitive milieu of contemporary technology startups—where first-mover advantage is often fleeting and codebases may represent the totality of a firm’s monetizable assets—the protection of source code is not merely a technical best practice; it is a fiduciary responsibility. The use of code obfuscation should be viewed as one component of a broader strategic posture encompassing secure development practices, intellectual property management, and cybersecurity risk mitigation.
Programmers obfuscate (from the Latin obfuscātus) source code to prevent it from being stolen, make it more difficult to tamper with, and secure valuable or sensitive information about the function of the code.
Unlike encryption, obfuscation only makes data difficult to understand for humans. Since the data remains machine-readable, obfuscating source code protects the code from cybercriminals without adding extra steps like de-encryption that may slow down the program’s run time.
In the competitive world of technology-based startups, intellectual property is often the highest-value asset a company owns. Implementing obfuscation techniques is an essential step to protecting IP from theft by competitors.
Why Is Source Code So Hard to Protect?
Typically, valuable data and information are protected by restricting access.
For example, sensitive client files are kept secure in password-protected, encrypted accounts that are difficult or impossible for criminals to breach.
However, source code is visible to anyone using a program, so access prevention methods can’t be used to secure the code or any information stored within it.
Instead, programmers can “disguise” the code via obfuscation so that it looks nonsensical to humans but is still machine-readable. This will prevent hackers from misusing the code while allowing the program to run as designed.
Obfuscation software can be used to automatically apply different obfuscation methods to sections of code, or programmers can select portions of data and obfuscate them by hand.
How to Obfuscate Source Code & Data
There are many different methods for obfuscating data. To strengthen code protections, programmers can mix and match different techniques throughout the code to make it even more difficult for hackers to read.
Below, we’ve outlined some of the more common techniques for effectively obfuscating data.
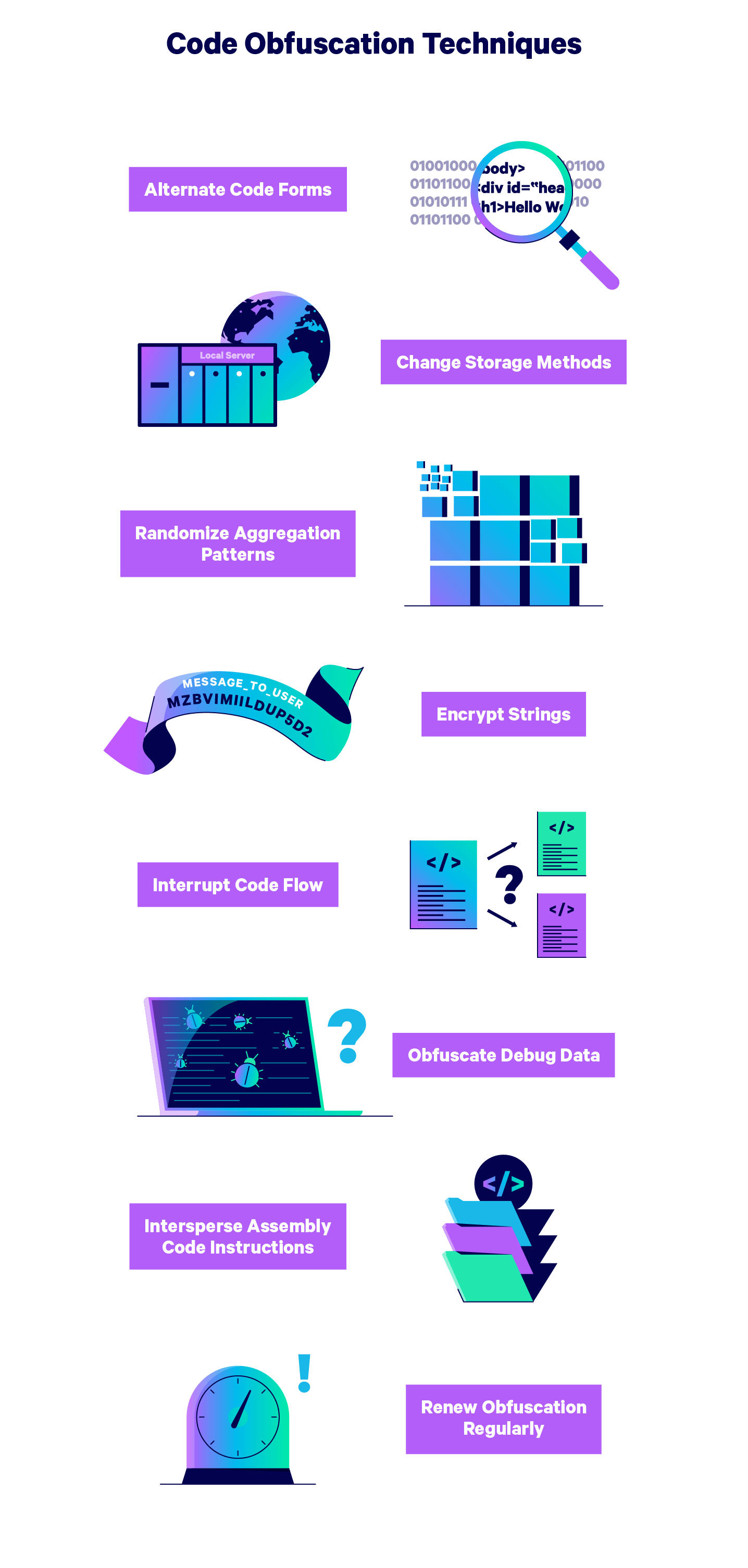
1. Alternate Code Forms
Translate short sections of the code into different forms throughout the program to make deciphering it more difficult without affecting run time.
For example, you can translate parts of your code to binary language, or replace a function with a table lookup of all possible values the function might produce.
2. Change Up Data Storage Methods
Make your data more difficult to read by essentially “hiding” your data using different memory types and locations. Alternate between storing variables locally and globally to conceal how the variables work together.
You can also randomize the addresses at which parts of code are located to create an additional level of confusion and make the code more difficult to read.
3. Randomize Aggregation Patterns
Another way to confuse hackers is by packaging your data in random sizes. For example, you might break arrays into an unnecessarily high number of sub-arrays to confuse any reverse engineering attempts.
4. Encrypt Strings
Though encryption isn’t an effective method for protecting your entire source code, you can use encryption as part of the obfuscation process without slowing the program.
Select individual keys, code strings, and other pieces of information to encrypt to create hacker “blind spots” in the code.
5. Interrupt Code Flow
Add unnecessary statements or “dead code” to your program to make it difficult to figure out what parts of the code contain real data.
Dummy code can also be used to conceal the pathways by which program control is passed between sections of the codebase.
6. Remove Debug Data
Debugging information can be used by hackers to reverse engineer a program’s source code, so it’s wise to obfuscate debug information by changing line numbers and file names.
Alternatively, you can entirely remove debug information from your program.
7. Obfuscate Assembly Code
Concentrate obfuscation efforts on assembly code to make it especially difficult to reverse engineer.
Many programmers like to hide assembly code within other code in a sort of Russian nesting doll pattern called the “jump-in-the-middle” technique, which will prevent a disassembler from producing the correct outputs.
8. Renew Obfuscation Tactics Regularly
Employ a schedule of obfuscation tactic renewal and refresh the techniques you’ve used throughout the code.
Vary the pieces of information you’ve hidden and encrypted, and alternate between tactics in different portions of the code.
Using multiple tactics to thoroughly obfuscate source code and refreshing obfuscation regularly will protect your startup’s IP from the majority of potential hacks.
However, no security measure can guarantee your startup’s safety, which is why it’s important to complement your cybersecurity precautions with comprehensive tech insurance that should include cyber liability, tech errors & omissions, and commercial crime insurance to protect your tech startup from all possible forms of cyberattacks.
By pairing your programmer’s attack prevention efforts with protection against a worst-case scenario, you’ll be able to keep your company safe no matter what happens.
To learn more about the policies that are right for your business, check out Embroker’s digital insurance platform.