A guide to data security for law firms
Law firms are targeted by hackers due to their sensitive information. Learn strategies to prevent attacks with our tips on cybersecurity for law firms.
The average person might assume the files on a lawyer’s laptop are essentially a bunch of boring documents, but hackers know the hard truth about that hard-drive.
Lawyers must adhere to attorney-client privilege which means any information a client shares with their attorney is to remain confidential — therefore, any testimony or information given by the lawyer is inadmissible in court.
Essentially, what this means is that lawyers have access to trade secrets, intellectual property, and figurative skeletons in the closets of their clients. And while it’s not a stretch to think that a multinational corporation can afford a sophisticated cybersecurity strategy, many law firms either cannot afford much in the way of cybersecurity or do not prioritize it.
This is why law firms have become targets within the hacker community. They contain all the desired information with less cybersecurity, on average.
In this guide to data security for law firms, we detail what obligations lawyers have to their clients regarding data protection, the risks of being hacked, examples of cyberattacks, and strategies to prevent, detect, and defend against intrusions.
Obligations and responsibilities for law firms
The American Bar Association (ABA) has held lawyers to the ethical and model rules of professional conduct since they were approved in 1983. These rules are the internal compass for lawyers to use when navigating various scenarios and interactions with clients.
Rule 1.6, regarding the confidentiality of client information, states that, “A lawyer shall make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client.”
Basically, this means lawyers must make efforts to protect their clients’ data.
In 2018, the ABA issued Formal Opinion 483, which discusses the importance of data protection and how to handle the inevitable security breach. The opinion states matter-of-factly that the risk of law firms experiencing a data breach is not if, but when. The opinion outlines requirements for before, during, and after a cyberattack targeting law firms:
As you can see, there are regulations in place that lawyers must make reasonable efforts to protect their data, react when a breach is suspected or detected, and inform any clients that may have been impacted by the breach.
In the sections to follow, you’ll see just how prevalent the risks are for law firms, case law that shows how liable law firms are for data breaches, and tips to increase your firm’s security processes.
Risks of attack
The threat landscape for law firms, and businesses more generally, has increased as more and more of our daily life and work is conducted online.
Just consider one of your firm’s top attorneys and how they allocate their time during work and life. Perhaps they start the day by checking email, update their status on Facebook, make a client call, and send a follow-up email with sensitive information attached. Not one, but every single one of these actions exposes information that hackers can use to infiltrate your law firm.
They may have fallen victim to email spoofing, which forges the sender and can include malicious attachments or links. Hackers could use their Facebook status to tailor a hack based on location or personal information to identify potential passwords.
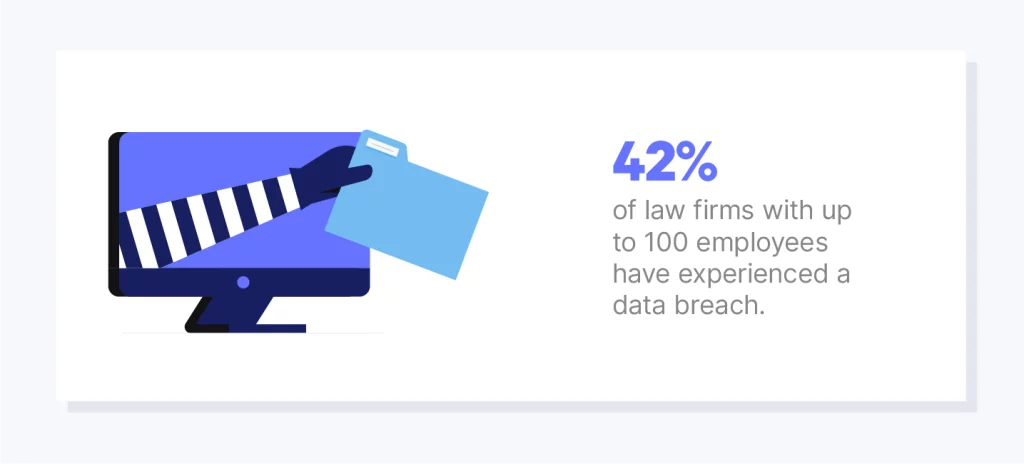
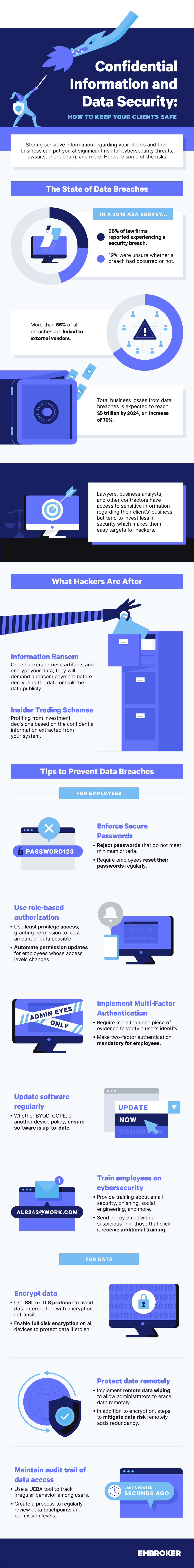
Cyberattacks against law firms are not a new phenomenon, but the rate of incidence and year-over-year growth is staggering. In fact, according to the ABA, up to 42% of law firms with up to 100 employees have experienced a data breach.
We’ve already discussed why hackers target law firms (because they typically have information hackers want from their clients, with less security), but we haven’t discussed their motives for obtaining this information.
1. Information ransom
Most hackers seek financial gain in one way or another. Hackers see the value of the information to your law firm as leverage for extracting money (likely cryptocurrency).
Once they have breached your database, retrieved the artifacts, and encrypted the data, they will send a notice of ransom before decrypting the data with the threat of releasing the information publicly. The public release of this information can have long-lasting repercussions, such as financial or physical damage to clients, damages to your firm’s reputation, and malpractice lawsuits from clients.
2. Insider trading schemes
Another method for hackers to profit from the data they extract from your firm is to make investment decisions based on the confidential information regarding your clients such as financial statements, mergers and acquisitions, financing deals, lawsuit potential, and more.
For example, your client is in the process of acquiring a top competitor and, if the deal is successful, will materially impact the stock price. If a hacker accessed pertinent information surrounding the deal, they could use that to buy (or sell) the stock based on this insider information.
Other risks and consequences of data breaches are a hacker bringing down your network, restricting access to information required for your work, or otherwise disrupting your billable hours. If you or your associates can’t access the necessary information to conduct client work, then your billables will suffer.
Other costs and consequences include hardware replacement, cybersecurity consulting fees, and, of course, client churn.
Hackers can come from a number of sources. There are nation-state actors who are acting on behalf of another country to manipulate the market or leverage information geopolitically, organized crime looking to exploit information for financial gain, or compromised insiders.
Examples of law firms under cyberattack
1. Wengui v. Clark Hill Law Firm
In 2016, Chinese businessman and political dissident, Guo Wengui, hired the international law firm Clark Hill to help apply for political asylum in the US. Wengui explained to the team at Clark Hill that the Chinese government had made him the target of ongoing cyberattacks and that it was likely they would experience similar attacks.
Sure enough, on September 12, 2017, Clark Hill’s servers were hacked, compromising Wengui and his wife’s passport information and their application for political asylum, which was then shared online. The hacks were widely believed to be orchestrated by the Chinese government.
After this event, Clark Hill tried to absolve itself of any liability by dropping Wengui as a client. Wengui then brought a $50 million suit against Clark Hill for breach of fiduciary duty, breach of contract, and legal malpractice.
The case is ongoing but the court held that Wengui pleaded viable claims for malpractice.
2. The Panama Papers
One of the largest data breaches of all time occurred back in 2016, in which more than 2.6 terabytes of data, or 11.5 million documents, were extracted from the international law firm Mossack Fonseca with headquarters in Panama.
The breach exposed data regarding the firm’s participation in forming shell companies for offshore wealth management. Many world leaders were implicated in the breach, including Russian President Vladimir Putin, who was linked to $2 billion in offshore accounts.
3. Class Action Suit for Threat of Data Breach
Over the last few years, lawsuits have begun to emerge based on the threat of data breach, even before any data has been compromised.
For example, Chicago based law firm Johnson & Bell is the defendant in an ongoing case where the plaintiff argues their web portal is vulnerable to attack and therefore continues to put client information at risk.
Johnson & Bell argue their system is secure, but their servers are running on an outdated JBoss software that has known vulnerabilities. With clients in the healthcare, insurance, and other industries, Johnson & Bell have significant targets in the form of sensitive business information such as financial statements, merger and acquisition deals, and more.
If the judge rules in favor of the plaintiff, a new precedent will be set regarding how law firms are expected to manage and maintain client data.
Security audits
There are two kinds of security audits: internal and external. The former is conducted by your team, the latter by external auditors.
Below, we provide a checklist for your internal audit:
-
- Planning
- Create an inventory of what is included in the audit
- Hardware devices
- Software integrations
- Database permissions
- Networks
- Outline Data classified by sensitivity
- Use Threat Modeling to identify threats and possible entry points.
- Create an inventory of what is included in the audit
- Employees
- Train employees on security processes and how to detect suspicious activity including:
-
- Phishing
- Social engineering
- Suspicious links and email spam
- Password security
- Processes for managing breaches
Tip: Send a company-wide email with a suspicious-looking link, employees that click on it receive additional training.
-
- Establish a standard device policy
- BYOD: Bring your own device
- COPE: Company-owned personally enabled
- Determine least privilege access: Employees only have access to information absolutely necessary for their jobs.
- Train employees on security processes and how to detect suspicious activity including:
- Vendors and Partners
- Understand the privacy policies and data security of all vendors and partners
- Have multiple points of redundancy and backups
- Planning
Why? Almost two-thirds of breaches are linked to external vendors*
-
- IT Department
- Have a plan for system hardening, which is the process of eliminating unnecessary nodes, accounts, permissions, access, or other unused potential vulnerabilities
- Application hardening
- Operating system hardening
- Server hardening
- Database hardening
- Network hardening
- Regular penetration testing: simulated cyberattacks to expose potential threats
- Anti-virus installed and auto-updates enabled
- Process for regularly reviewing error logs
- Environment variables, code review, and version control best practices reviewed
- Consult a third-party to double-check your IT team’s work
- Have a plan for system hardening, which is the process of eliminating unnecessary nodes, accounts, permissions, access, or other unused potential vulnerabilities
- Physical Security
- Keep servers in a locked and secure location
- Store your remote backups in a separate and safe location
- Establish a process for regular inspection
- Install biometric or keycard access and security camera systems
- Ensure the process of device and file disposal is safe and permanent
- Data Security
- Data encryption
- At rest
- In transit
- SSL for internet data transfers
- Establish a Process for Auditing at Regular Intervals
- Quarterly internal audits
- Annual external audits
- Data encryption
- IT Department
Data and security policies
Many people ask, “how do I know if my account information has been compromised?”. The very nature of this question assumes a hacker has already breached the system and a method of detection is all you need. This is a retroactive mindset: You should strive to be more proactive by forming systems and processes for prevention.
Let’s cover some policies that can help prevent attackers from exploiting vulnerabilities in your systems.
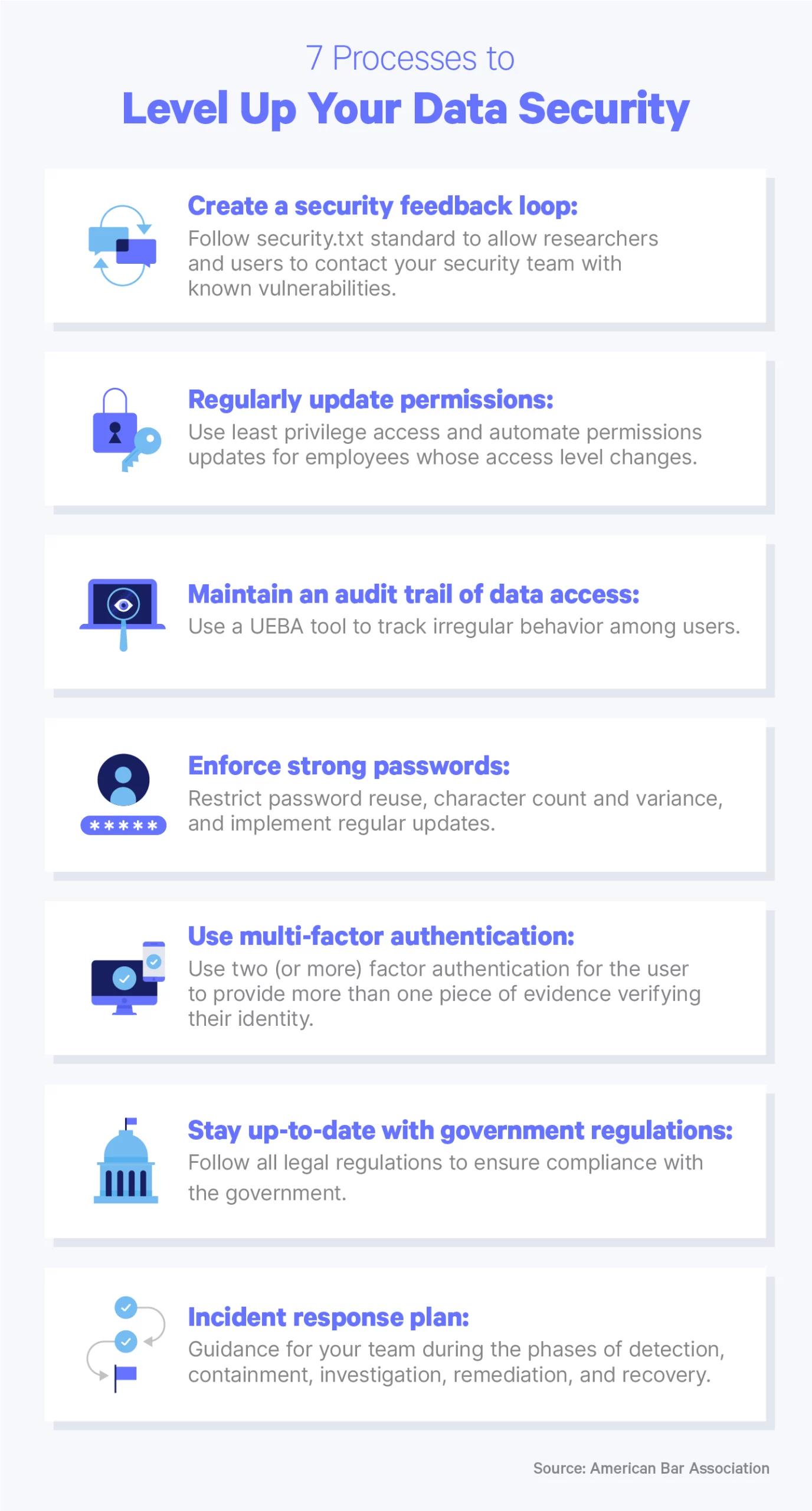
1. Create a security feedback loop
Having an email address for users to contact your security team if a vulnerability is believed to exist can help avoid exploits down the line. Some companies even offer a bug bounty, where they incentivize security experts to alert them of potential issues and receive compensation, instead of simply exploiting the bug for financial gain.
A growing number of sites are implementing a security.txt standard, which offers a centralized place for sites to define their security policies. This can help individual security researchers who find vulnerabilities quickly and easily report them.
2. Regularly check and update permissions
Not everyone in your organization needs a key to every door in the building, hypothetically speaking. When considering what level of access each employee should have, you should consider the minimum level of access possible. Or to continue with our example, figure out the minimum number of doors this person needs access to, and give them keys to those doors and those doors only. This is known as least privilege access.
You can automate the process of re-certification and/or revocation of access. This process becomes especially important when employees get promoted or resign. You should have a recurring event when all permissions within the company are re-evaluated.
3. Maintain an audit trail of data access
It’s important to have a process in place to track irregularities in regard to data touchpoints to help highlight when an administrator’s account has been compromised, the employee has gone rogue, or any number of other scenarios.
A User and Entity Behavioral Analysis (UEBA) tool, uses sophisticated machine learning algorithms to analyze and highlight any unusual activity within your organization.
For example, if an IT Manager has historically downloaded 100 MB of data on a daily basis to run reports, your UEBA tool would signal if and when a deviation of significant magnitude occurred. For example, if one day the IT Manager downloaded 100 GB of data (1,000x) this would trigger an alert.
4. Enforce strong passwords
One of the most common entry points for hackers is through insecure passwords. If you have ever used “password” as a password or reused a password for more than one account login, you are not alone. According to a survey by Google, 65% of users reuse passwords for multiple, if not all, accounts.
When creating a password, ensure your system has a validation in place to reject passwords that do not meet minimum criteria. It’s also recommended that you have employees, clients, and anyone else with access to your system reset their passwords regularly.
5. Use multifactor authentication
Many breaches could have been thwarted by multifactor authentication. The most common form is two-factor authentication, where the user must provide at least two pieces of evidence regarding their identity.
Commonly, when a user is logging into a web portal, a unique code will be sent via an SMS text message to verify the person logging in has access to the phone number on file. Other forms of multifactor authentication include security questions, captcha, and more. Ensure your insurance will cover in the event of a security breach.
6. Stay up-to-date with government regulations
Data and privacy have taken center stage in many regulatory arenas around the world. From GDPR in Europe to CCPA in California, understanding how to comply with regulations where you practice law is essential to protect your clients and their data.
For example, to be GDPR-compliant, a company is legally required to have a nominated Data Protection Officer responsible for the inflows and outflows of data.
7. Incident Response Plan
The incident response plan is how your team will handle the various phases of attack, including:
- Detection: Discovery of the event through software tools, unusual activity, or reports by personnel or outside sources.
- Containment: The triage stage where the compromised component is identified and isolated.
- Investigation: Determine the entry point and scope of the attack.
- Remediation: Repair systems affected by the breach, notify affected parties, report to law enforcement if necessary, conduct a post-mortem of the attack.
- Recovery: Use the lessons learned from this attack to iterate your process and improve.
Read our related guide on developing a cyberattack response plan for your law firm for more information.
Tips on cybersecurity for law firms
With the threat of malpractice for mishandling your client data, implementing processes to prevent data security breaches is the most responsible course of action after having adequate professional liability insurance coverage.
Here are some tips for your law firm to lower the chances of getting hacked:
Conclusion
The number of law firms reporting cyber insurance declined by 1% from 2018 to 2019, despite the projection that cybercrime will increase by 70% over the next 5 years.
It’s clear that law firms are under a constant threat of cybercrime and must take steps to defend their clients’ data. Don’t wait until it’s too late, take steps today to create a cybersecurity policy and prevent future data breaches and the consequences that follow. Akin to the need for having adequate malpractice insurance for your law firm, having adequate data protection and cyber insurance for your law firm is essential. You can learn more about other policies you might need in our guide to insurance for law offices.